介绍使用Certbot获取SSL/TLS证明书的方法。CA(证书颁发机构)使用Let’s Encrypt,是大部分浏览器信任的CA。操作所需时间是3分钟左右。
- Let’s Encrypt仅提供DV(Domain Validation)证书,而不颁发OV(Organization Validation)和EV(Extended Validation)证书。(因为无法自动化证书颁发流程)
- Let’s Encrypt是非营利团队,因此颁发的证书可免费使用。
- Let’s Encrypt发行的证书的有效期限是90天。
前提条件
在签发SSL/TLS证书时,认证颁发机构需要验证是否拥有该域名。Let’s Encrypt通过从该域名的特定路径下载验证文件并验证其内容来确认该域名所有权。准备Let’s Encrypt需要的验证文件并与进行通信的就是Certbot。
- DNS解析已完成
- 在安装证书的服务器上进行操作
- 该服务器上需要运行Web服务(Nginx或者Apache等)
获取moto.sys-blog.net域名的证书时,需要满足以下条件。
DNS解析是否已生效
# dig moto.sys-blog.net
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.amzn2.5.2 <<>> moto.sys-blog.net
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3509
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;moto.sys-blog.net. IN A
;; ANSWER SECTION:
moto.sys-blog.net. 300 IN A 43.206.85.203
;; Query time: 40 msec
;; SERVER: 192.168.0.2#53(192.168.0.2)
;; WHEN: Fri Sep 09 23:20:37 UTC 2022
;; MSG SIZE rcvd: 62
确认DNS解析的服务器是否和Certbot获取证书的服务器一致
# curl ifconfig.io
43.206.85.203
HTTP访问该域名
# curl -I http://moto.sys-blog.net
HTTP/1.1 200 OK
Server: nginx/1.20.1
Date: Fri, 09 Sep 2022 23:21:26 GMT
Content-Type: text/html
Content-Length: 732
Last-Modified: Thu, 07 Dec 2017 20:57:37 GMT
Connection: keep-alive
ETag: "5a29ab41-2dc"
Accept-Ranges: bytes
获取SSL/TLS服务器证明书
在Web服务器仅获取证明书,Web服务器的SSL的设定手动进行。使用OS为Amazon Linux2,Web服务器为Nginx。Web服务器为Apache时,需要安装python2-certbot-apache。
# amazon-linux-extras install epel
# yum install certbot python2-certbot-nginx
certbot certonly命令获取证明书,-w选项指定网站根目录,-d选项指定域名。如果想把证书自动配置到nginx的配置文件使用certbot –nginx命令。
# # certbot certonly --webroot -w /usr/share/nginx/html -d moto.sys-blog.net
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): admin@moto.sys-blog.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017-w-v1.3-notice.pdf.
You must agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Account registered.
Requesting a certificate for moto.sys-blog.net
Performing the following challenges:
http-01 challenge for moto.sys-blog.net
Using the webroot path /usr/share/nginx/html for all unmatched domains.
Waiting for verification...
Cleaning up challenges
Subscribe to the EFF mailing list (email: admin@moto.sys-blog.net).
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/moto.sys-blog.net/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/moto.sys-blog.net/privkey.pem
Your certificate will expire on 2022-12-09. To obtain a new or
tweaked version of this certificate in the future, simply run
certbot again. To non-interactively renew *all* of your
certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
获取的证书保存在 /etc/letsencrypt 目录。
# tree /etc/letsencrypt/
/etc/letsencrypt/
├── accounts
│ └── acme-v02.api.letsencrypt.org
│ └── directory
│ └── 517f2571e56afb6f54c295378a51cc97
│ ├── meta.json
│ ├── private_key.json
│ └── regr.json
├── archive
│ └── moto.sys-blog.net
│ ├── cert1.pem
│ ├── chain1.pem
│ ├── fullchain1.pem
│ └── privkey1.pem
├── csr
│ ├── 0000_csr-certbot.pem
│ ├── 0001_csr-certbot.pem
│ ├── 0002_csr-certbot.pem
│ └── 0003_csr-certbot.pem
├── keys
│ ├── 0000_key-certbot.pem
│ ├── 0001_key-certbot.pem
│ ├── 0002_key-certbot.pem
│ └── 0003_key-certbot.pem
├── live
│ ├── moto.sys-blog.net
│ │ ├── cert.pem -> ../../archive/moto.sys-blog.net/cert1.pem
│ │ ├── chain.pem -> ../../archive/moto.sys-blog.net/chain1.pem
│ │ ├── fullchain.pem -> ../../archive/moto.sys-blog.net/fullchain1.pem
│ │ ├── privkey.pem -> ../../archive/moto.sys-blog.net/privkey1.pem
│ │ └── README
│ └── README
├── renewal
│ └── moto.sys-blog.net.conf
└── renewal-hooks
├── deploy
├── post
└── pre
15 directories, 22 files
手动设定Nginx的SSL证书,需要使用以下2个文件修改/etc/nginx/ngingx.conf文件。
- /etc/letsencrypt/live/moto.sys-blog.net/privkey.pem
- /etc/letsencrypt/live/moto.sys-blog.net/fullchain.pem
# For more information on configuration, see:
# * Official English Documentation: http://nginx.org/en/docs/
# * Official Russian Documentation: http://nginx.org/ru/docs/
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 4096;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
# See http://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*.conf;
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name moto.sys-blog.net;
root /usr/share/nginx/html;
ssl_certificate /etc/letsencrypt/live/moto.sys-blog.net/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/moto.sys-blog.net/privkey.pem;
# Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
error_page 404 /404.html;
location = /404.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
}
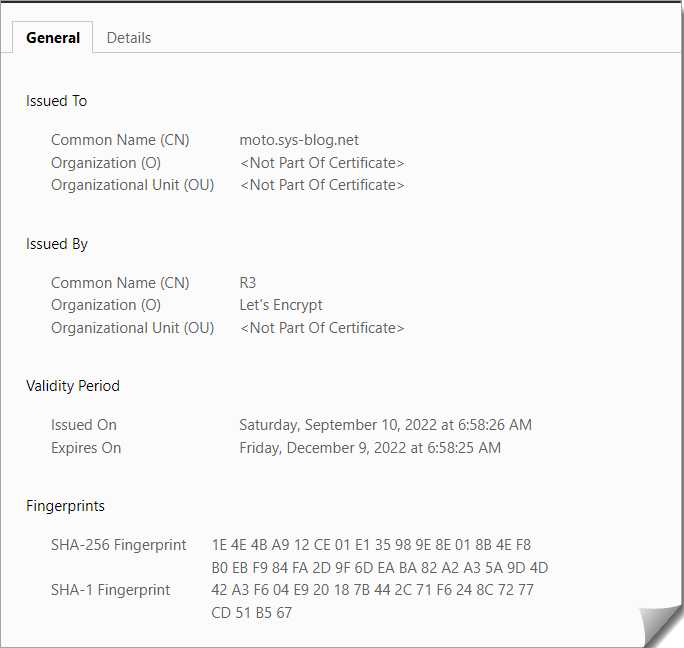
打开浏览器访问 https://moto.sys-blog.net ,确认到的证书内容如下。